By cuterose
Ericsson UDM extends 5G core authentication solution with hardware security module
Ericsson Authentication Security Module: in a nutshell
The importance of user privacy and security are continuously growing with 5G. New use cases, different access types (for example, 3GPP, non-3GPP, Wi-Fi, 3G, 4G and 5G), and the evolving infrastructure of communication service providers (CSPs), are increasing security demands across the network domain. As a result, we need to look at how to make the users’ authentication information more secure.
With 5G networks growing in number around the globe and becoming a core part of many countries’ critical infrastructure, user authentication and security are bringing ‘stickiness’ to stricter laws and regulations that are aimed at controlling network access and protecting user data. The adoption of technologies, such as cloud and network slicing, and the wider variety of devices and access-networks, adds complexity to the infrastructure and increases the types of authentication use cases that need to be more securely handled.
The current standardized solutions will be under stress in the 5G wider ecosystem, resulting in increased networks vulnerability risks.By integrating an Hardware Security Module (HSM) to the 5G core, Ericsson is providing CSPs with a stronger cryptographic key and algorithms protection in a tamper-resistant hardware.
Why will CSPs require authentication security HSM?
While security has always been a hot topic in mobile networks, the security focus is intensifying with 5G. This is because 5G will result in billions of new devices being connected to mobile networks. These devices will increase network exposure by having different characteristics, different types of access points and different security mechanisms.
The new types of 5G use cases, as well as deployment scenarios that may involve network slicing, edge computing, private networks, etc., will also present new levels of exposure and challenges on security.
Figure 1 - Authentication security spreads across multiple contexts and use-cases
The cloudification of the networks moving important workloads and user traffic is another factor that will lead to increased security risks.
In the last few years, we’ve also seen an increasing number of cyberattacks on networks, and these are becoming more sophisticated over time.
As 5G networks become a key component in a country’s critical communication infrastructure, the business risks increase, as a result, national regulators need to counter-attack by increasing their mandates and requirements for network security.
On the other hand, with more demanding use cases, attack motivations are increasing, and the attack vectors are multiplying. With significant value at stake, the tolerance for security risks is decreasing.
But are the current standardized authentication solutions safe enough?
While existing software-based authentication solutions for mobile networks are very safe for most of the 5G use cases, they may not be strong enough for certain 5G use cases and/or markets that have more strict security requirements.
For use cases that provide very critical services, such as remote surgery and mission critical communication, an extended level of security may be desired. Currently, the industry is working on establishing methods to achieve similar trust and security as in embedded systems. For instance, by including hardware technologies such as HSM on 5G networks.
Encryption mechanisms rely on cryptographic keys, identifiers, credentials (collection of usernames and passwords), and encryption algorithms that are stored in the 5G core network. However, implementation aspects of such mechanisms in the 5G system are only standardized by 3GPP to a very limited degree.

To safeguard the network from malicious access, 3GPP's 5G system standards provide security mechanisms that are based on well-proven 4G security mechanisms, but also include new enhancements for e.g., encryption, authentication, and user privacy. For example, with 5G we see the introduction of international mobile subscriber identity (IMSI) encryption where all traffic data sent over 5G radio network is encrypted, integrity protected and subject to mutual authentication e.g., device to network.
In virtualized deployments, multiple vendors may also be involved in providing different parts of the solution such as the hardware infrastructure, the virtualization platform, and the applications that execute the 3GPP network functions. Secure provisioning and storage of identifiers and credentials is an integral part of providing a secure deployment in virtualized deployments. Currently, the industry is working on establishing methods to achieve similar trust and security as in embedded systems, for example by including hardware technologies such as HSM.
In summary, CSPs will look at added authentication security in UDM solution for:
Figure 2 - Increased complexity when managing authentication and privacy in 5G
How does the Ericsson Authentication Security Module address these challenges?
The new Ericsson Authentication Security Module is a premium security offering that includes a physical dedicated module for central management of authentication procedures in 5G Core networks. It offers:
I liked a @YouTube video from @kerondisney https://t.co/AvZICb5XAf HOW TO REMOVE SCOOTER WHEELS AND REPLACE THEM
— razzer Wed Oct 19 18:40:25 +0000 2016
It allows moving the sensitive part of the authentication software, such as cryptographic keys and encryption algorithms, to an external and dedicated hardware storage environment (i.e., HSM) to augment the security for network authentication and end-user privacy protection.
The Ericsson Authentication Security Module is composed of the Authentication Credential Repository and Processing Function (ARPF), which centralizes all authentication procedures in the core network. It’s powered by the 5G Luna HSM component provided by Thales, the industry leader in the HSM market and a global presence in multiple sectors.
It provides the highest level of security through a tamper resistant hardware platform, certified FIPS 140-2 Level 3, that meets compliance requirements and a wide array of regulations.
With one combined solution, the Ericsson Cloud Core Subscription Manager provides highly secure authentication mechanisms to enable premium protection of the users’ privacy.
Figure 3 - Ericsson Authentication Security Module product view
Ericsson launched its Authentication Security Module solution to broaden security for user privacy, based on a physical dedicated module for central management of authentication procedures in 5G Core networks.
Ericsson’s approach for providing HSM-based authentication
Authentication is a security process to get cryptographic assertion that the device (for example, a mobile phone or IoT device) and the network are the entities they’re claiming to be – this is called a mutual proof authentication.
The network cryptographically authenticates the device allowing the CSPs to ensure that: the specific services are provided to the correct users, the users cannot deny their bill and one user cannot impersonate another user.
The authentication procedure is performed using a key identifier and authentication algorithms commonly referred by the 3GPP term ‘authentication and key agreement’ (AKA).
Subscriber privacy is another security process implemented in 5G networks to conceal/ hide, the subscriber’s identity in the initial attach to the network.
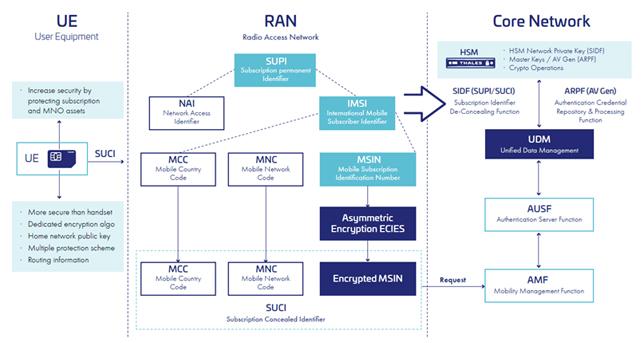
Instead of sending the subscription permanent identifier (SUPI) over the air, the user equipment (UE) sends a concealed version of the SUPI called a subscription concealed identifier (SUCI). The SUCI is created by the UE based on public key cryptography.
The UE shall generate a SUCI using a protection scheme with the home network public key, that was securely provisioned to the UE in control of the home network. The home network (UDM/SIDF) can then derive the SUPI from the SUCI by using the home network private key.
Figure 4 - Principles of Authentication and Subscriber Privacy
As mentioned earlier, the complexity and the variety of authentication use cases significantly increases in 5G core networks. New network elements are introduced for authentication in 5GC architecture as the UDM, ARPF and AUSF must interwork with the existing elements in the 3G and 4G architectures. In Figure 5, below, we illustrate the difference that occurs when the HSM is or isn’t used in the network.
Figure 5 - Authentication Vector Generation without Ericsson Authentication Security Module
Figure 5 shows the standard 3GPP 5GC solution where the ARPF centralizes and performs all authentication procedures interfacing the rest of the network via the unified data management (UDM) function. In this typical scenario, the ARPF also stores and manages all cryptographic keys and algorithms, performs vector generation and cares for the subscription de-concealing function in 5G. However, in figure 6, below, when the HSM component is added the ARPF still acts as the central point towards the rest of the network, but now it implements extra mechanisms: enabling it to interface with the external HSM module. The subscription de-concealing function, authentication generator function and the storage of keys and algorithms are them transferred to the HSM.
Figure 6 - Authentication Vector Generation with Ericsson Authentication Security Module
HSM is a crypto processor that is specially designed and dedicated to protecting the crypto key lifecycle. It’s a hardware device that manages and safeguards the cryptographic authentication process.
Organizations that require higher levels of security to manage, process and store cryptographic keys use these modules. HSM provides logical and physical protection to digital keys from unauthorized users.
The Authentication Security Module is seamlessly integrated to Ericsson’s dual-mode 5G Core: a cloud-native, microservices-based technology that combines Evolved Packet Core (EPC) and 5G Core (5GC) network functions into a common multi-access and cloud-native platform that supports both 5G and previous generations for optimized footprint and total cost of ownership (TCO) efficiency - via Ericsson CCSM (Cloud Core Subscription Manager) and provides full interwork with the legacy networks and network functions.
As it is pre-integrated, tested and validated, it considerably reduces the time-to-market (TTM) and the need for additional activities in field.
However, as mentioned earlier, the HSM component of the solution is not part of 3GPP standard architecture. Also, due to its purpose of providing extended security with a physically dedicated hardware, it’s not deployed as a cloud-native function.
Figure 7 – Ericsson’s cloud-native dual-mode 5G Core product view
Benefits of the Ericsson Authentication Security Module
To summarize, the Ericsson Authentication Security Module:
- Centralizes and consolidates authentication vector generation for 3G, 4G and 5G accesses in a seamless integrated solution into our 5G Core offering.
- Provides a premium level of security in 5G networks, allowing the storage and management of all crypto keys and algorithms combining the strengths of Ericsson’s 5G Core Subscriber Data Management solution and Thales market leading HSM.
- Is compliant with major security standards in the industry and adds a compliance stamp to CSPs who are operating in markets with stricter regulatory requirements.
- Enables a safer industry eco-system for use cases innovation in 5G by addressing the needs of verticals with very strict security requirements – from developers to consumers in the eco-system chain.
- And finally, as part of Ericsson’s CCSM offering, it secures all required integration quality and support within one TCO.
Learn more
Visit the solution webpage HSM security in 5G core networks, watch the video, and download the solution brief.